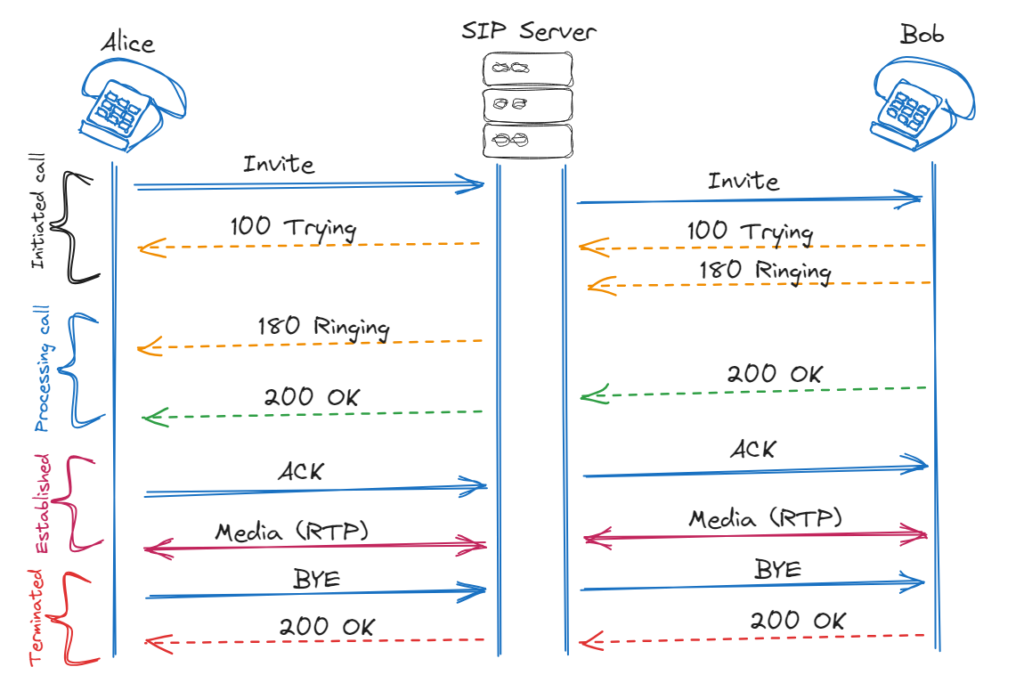
Session Initiation Protocol (SIP) is a signaling protocol used in Voice over IP (VoIP) communication systems1. It facilitates establishing, modifying, and terminating multimedia sessions between participants over an IP network. SIP handles call setup, call control, and session management.
Here’s an overview of how the SIP protocol works:
- Session Initialization: When a user wants to initiate a communication session, such as a voice call or a video conference, their SIP client sends a SIP INVITE message to the intended recipient. This message includes details about the session, such as the participant’s SIP addresses.
- Session Establishment: The recipient’s SIP client receives the INVITE message and sends a SIP 200 OK response if the session can be established. This response contains the necessary information to set up the session, including the desired media parameters such as audio codecs, video codecs, and encryption method2.
- Session Control: During the session, SIP enables participants to control various aspects of the communication. For example, a user can send a SIP message to adjust the volume, mute or unmute the microphone, or add or remove participants from a conference call2.
- Session Termination: When a user wants to end a session, their SIP client sends a SIP BYE message to the other participants, indicating their intention to terminate the session. The other participants respond with SIP 200 OK messages, and the session is effectively terminated2.
SIP also supports additional functionalities such as call forwarding, call transfer, and presence information (indicating a user’s availability for communication)2.
It’s worth noting that SIP operates at the application layer of the TCP/IP protocol stack and typically uses port 5060 for unencrypted communication and port 5061 for encrypted communication using Transport Layer Security (TLS)1.
Overall, SIP provides the signaling necessary to initiate, modify, and terminate multimedia communication sessions over an IP network, enabling users to make voice and video calls, conference calls, and more.
In the context of malware analysis, SIP can be of interest for several reasons:
- Malware Command and Control (C2): Malware may use the SIP protocol to establish communication channels with command and control servers. It allows attackers to control and command the infected systems remotely. Analyzing SIP traffic can help identify suspicious communication patterns or unexpected connections.
- Malicious SIP Requests: Malware or attackers may generate malicious SIP requests to exploit vulnerabilities or launch attacks. For example, SIP-based attacks like SIP flooding or scanning can affect VoIP systems’ availability and integrity. Analyzing SIP traffic can help detect and mitigate such attacks.
- Malware Indicators: Analyzing SIP traffic can potentially reveal indicators of compromise (IOCs) related to malware infections. This could include suspicious SIP request patterns, unusual SIP header fields, or unexpected behavior in SIP message flows1.
By monitoring and analyzing SIP traffic, malware analysts can identify and investigate potential threats, monitor for malicious communication, and develop detection mechanisms to identify malware activity that leverages the SIP protocol.
Please note that the information provided is a general understanding of how SIP can relate to malware analysis. For more specific details and techniques used in analyzing SIP traffic, referring to specialized resources or research articles on the topic is recommended.