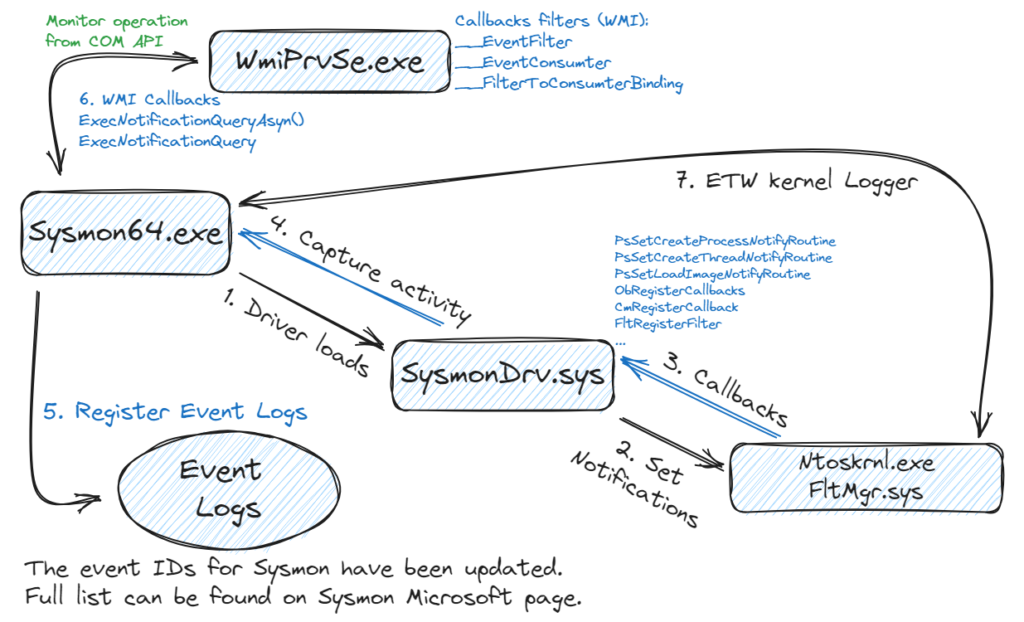
Sysmon (System Monitor) is a powerful Windows system utility developed by Microsoft’s Windows Sysinternals team. It provides extensive visibility and detailed system activity monitoring, aiding malware analysts in detecting and investigating malicious behavior on a Windows system. By capturing event information from various operating system components, Sysmon helps analysts gain insight into system and network activity, enabling them to identify indicators of compromise (IOCs) and detect potentially malicious behavior.
Sysmon operates by installing a kernel-level device driver on the system, which allows it to collect detailed information about system events. It generates logs that provide information, including process creation, network connections, file creation, registry modifications, DLL loads, and other system-level events. This data is crucial for real-time monitoring and forensic analysis during incident response investigations.
Here are some key features and benefits of Sysmon for malware analysts:
- Process Monitoring: Sysmon tracks process creation events, allowing analysts to monitor the execution of potentially malicious programs. This helps in identifying suspicious processes and understanding the execution chain of events.
- Network Connection Monitoring: Sysmon logs network connection events, providing visibility into network activity by capturing details such as source and destination IP addresses, ports, and protocols. Network monitoring helps analysts identify unauthorized communication and command-and-control (C2) channels used by malware.
- File and Registry Monitoring: Sysmon monitors file and registry events, capturing details about file creations, modifications, deletions, and access to specific registry keys. This helps analysts identify file-based or registry-based indicators of compromise and track changes made by malware.
- Command Line Monitoring: Sysmon records command line information for created processes, allowing analysts to observe the parameters passed to executables. This helps in understanding the behavior of executed programs and identifying suspicious or malicious command-line arguments.
- Integration with SIEM and Threat Intelligence: Sysmon logs can be easily ingested into Security Information and Event Management (SIEM) systems, enabling analysts to correlate and analyze the collected data. Additionally, Sysmon logs can be compared against known threat intelligence sources to identify potential indicators of compromise.
- Customization and Configuration: Sysmon offers various configuration options, allowing analysts to tailor the monitoring to specific needs. It can be customized and tailored to focus on specific event types or exclude certain events, reducing noise and optimizing analysis efforts.
By leveraging the power of Sysmon, malware analysts can enhance their ability to detect and analyze malicious activities on Windows systems.
It provides:
- A comprehensive view of system events.
- Aiding in identifying suspicious behavior.
- Investigating incidents.
- Strengthening overall security defenses.